What is a captive portal?
A captive portal serves as the primary mechanism for controlling access to a specific network, ensuring that only authorized users can connect and facilitating authentication for new users. Typically presented as a login page or password prompt, the portal allows users to authenticate themselves, gaining access to the network and enabling normal internet usage.
Additionally, captive portals are employed to showcase terms and conditions, or to deliver marketing messages to users before permitting network access. Beyond enhancing security, businesses can leverage these portals to gather valuable insights about customers entering their physical premises.
Captive portal example by Aiwifi
How do captive portals work?
In simpler terms, a captive portal is like a digital bouncer for a network. It blocks people from getting in until they prove they should be allowed. This proof can be a simple registration form or using social media or email accounts to sign in.
For users, it means filling out a form or logging in with their social media account to access the Wi-Fi at a business place. The information they provide is saved, making it easier for them to connect during future visits.
This setup benefits both the users and the business. Users get free internet access, and the business gets valuable information about its customers. By gathering this data, businesses can create detailed customer profiles, helping them make smarter decisions to improve the overall customer experience.
However, it's crucial for organizations to handle this data carefully, ensuring it's kept secure and only accessible to authorized people. Captive portals are just the starting point for collecting useful information.
In technical terms, the captive portal works like the following flow:
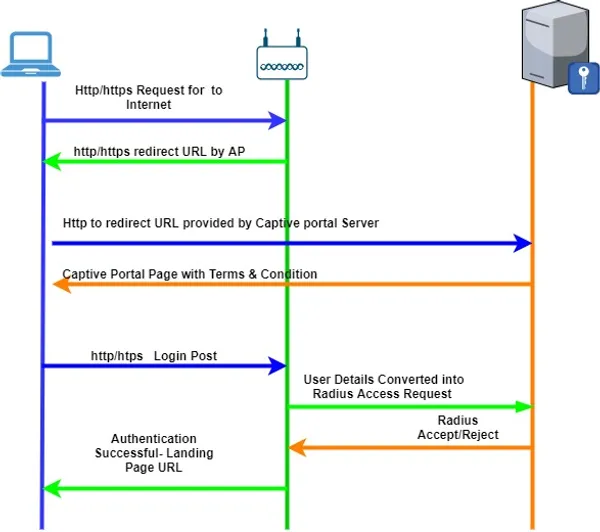
Important notes:
The captive portal is only responsible for allowing or denying Internet access. The infrastructure is still responsible for: providing an IP address, resolving DNS queries, managing QoS and other firewall rules and WiFi Client isolation amongst other possible configurations.